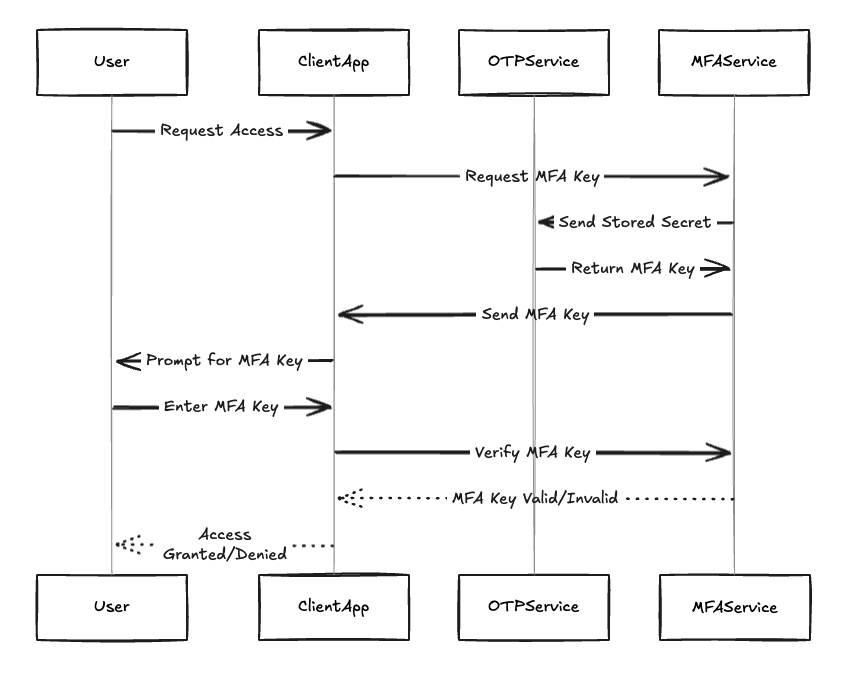
Multi-Factor Authentication (MFA) is a cornerstone of modern security. It protects user accounts by requiring a time-sensitive code, typically generated from a shared secret, on top of the traditional username and password. While indispensable in production, MFA can be a significant obstacle in test environments where automation, reproducibility, and team collaboration are paramount.
That’s where a stateless MFA-as-a-Service comes into play.
The Problem with MFA in Test Environments
In real-world scenarios, MFA is tightly coupled with a user's identity, device, and authentication app. While that’s ideal for end users, it introduces major friction for engineering teams:
- MFA codes change every 30 seconds – which makes scripted interactions difficult without a shared mechanism.
- Test accounts are often shared – among QA engineers, automation bots, and developers. Securely managing secrets across the team can be painful.
- CI/CD pipelines, Selenium/Watir tests, and API fuzzers – can’t easily interact with MFA flows unless the code can be retrieved programmatically.
- Using production-grade MFA systems in test environments is both risky and overkill.
The Solution: Stateless MFA-as-a-Service
A stateless MFA service allows engineers to pass a TOTP (Time-based One-Time Password) secret and receive the 6-digit code and expiration metadata in return. No state is stored. No registration is required. No sensitive user identity is associated with the request.
Sample API Call
GET /mfa?secret=BASE32ENCODEDSECRET
Sample Response
{
"code": "481516",
"time_remaining": 21,
"interval": 30
}
Key Benefits for Testing
1. Stateless and Secure by Design
No accounts, no sessions, and no stored secrets. This is a calculator, not a vault. As long as the secret is known, the code can be generated on demand. That keeps things simple and reduces the attack surface.
2. Enables Fully Automated MFA Testing
With a simple API call, CI/CD systems, API test harnesses, or browser automation frameworks can retrieve valid MFA codes without human intervention. This is critical for:
- Smoke testing MFA flows
- Validating login workflows
- Running full-stack integration tests that involve MFA
3. Shared Testing Secrets Across Teams
If your test accounts are shared among engineers, testers, or contractors, managing MFA secrets securely is a challenge. This system allows:
- Controlled, read-only use of secrets
- Decoupling of the secret from who or what is using it
- Eliminating the need to share a device or authenticator app
4. Ideal for Disposable and Ephemeral Accounts
Many test environments spin up and tear down accounts regularly. Tying those accounts to a mobile device or MFA platform isn’t scalable. A lightweight API-based approach enables dynamic use of MFA across:
- Sandboxed environments
- Integration testing VMs
- Short-lived cloud resources
What It’s Not For
This service is not suitable for:
- Production accounts
- Storing secrets
- Acting as a full authentication provider
In short: Do not use this for anything with real users, personal data, or financial impact. Its entire purpose is to support internal tooling, QA pipelines, and developer testing scenarios.
Closing Thoughts
In a secure development lifecycle, testing shouldn’t come at the cost of security, but security also shouldn’t paralyze testing. A stateless MFA-as-a-Service provides a middle ground: secure, simple, and effective for what it’s designed to do.
It’s a pragmatic tool in a modern DevSecOps pipeline, because while real authentication is serious business, testing it shouldn’t be unnecessarily hard.
Try it your self:
https://mfa.lets.qa/mfa?secret=JBSWY3DPEHPK3PXP
or
curl "http://mfa.lets.qa/mfa?secret=JBSWY3DPEHPK3PXP"